User authentication is how admins and developers like you and I enforce secure access to user accounts. But in the face of increasing cybersecurity concerns, our challenges have grown taller.
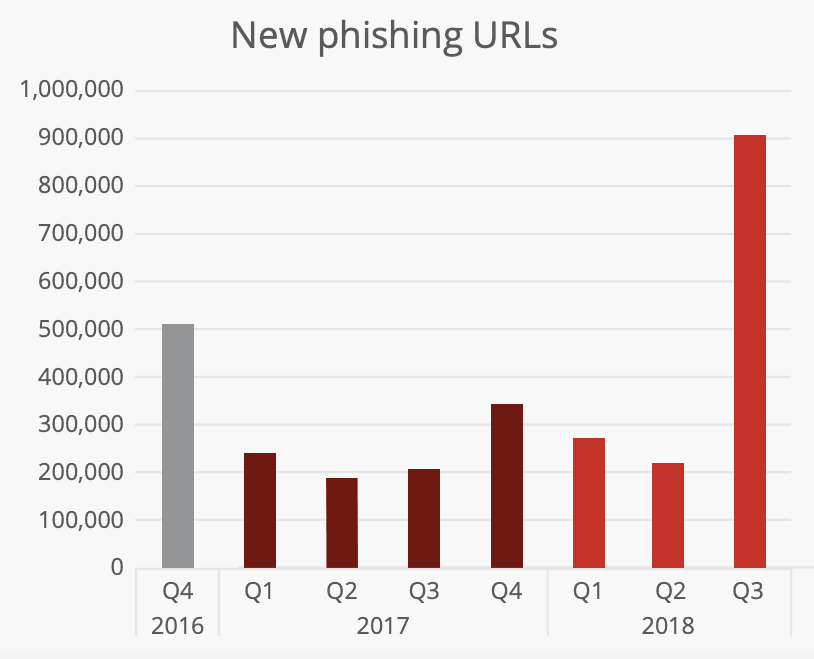
Look at the statistics. In the first three quarters of 2018 alone, attackers launched about 1.4 million phishing URLs. As you know, phishing targets a user’s authentication rights and identity.
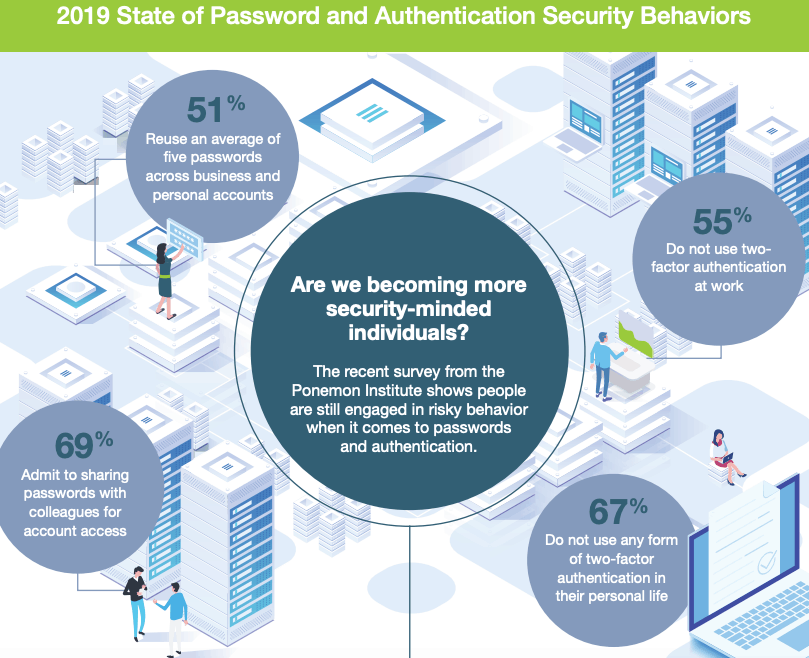
Meanwhile, in the real world, most people are not taking precautions to secure their accounts. In a study published in 2019, 67 percent of participants do not use two-factor authentication at all for their accounts. Out of those that use 2FA, 55 percent do not use it at work.
This laxity to security puts admins on edge. So this article identifies and provides solutions to some of the problems you face in implementing user authentication for your apps and websites.
1. Getting Users to Set Strong Passwords
The passwords of nine out of every ten employees can be hacked within six hours. And two-thirds of people use the same password for most of their accounts. So imagine a black hat hacker stealing that one password, and it’s the same password for your online banking.
The Problem with Getting Users to Set Strong Passwords

Users worry that they’ll forget their passwords all the time if they use unique passwords for each online account they set up. This fear deters them from following their admins’ suggestions even if they know better.
Most users don’t know that they can safely store passwords on a password manager. So far, it looks like admins haven’t done much in telling users about password managers.
The Solution for Admins and Developers
Tell your users about the dangers of using a single password or repeating passwords. Let them know that a secure password manager like KeePass, LastPass, or others saves them the stress of remembering passwords. These password managers also help them set strong passwords. Teach them how to use browser extensions for password manager of your choice.
2. Encouraging Users to Implement 2FA for Their Accounts
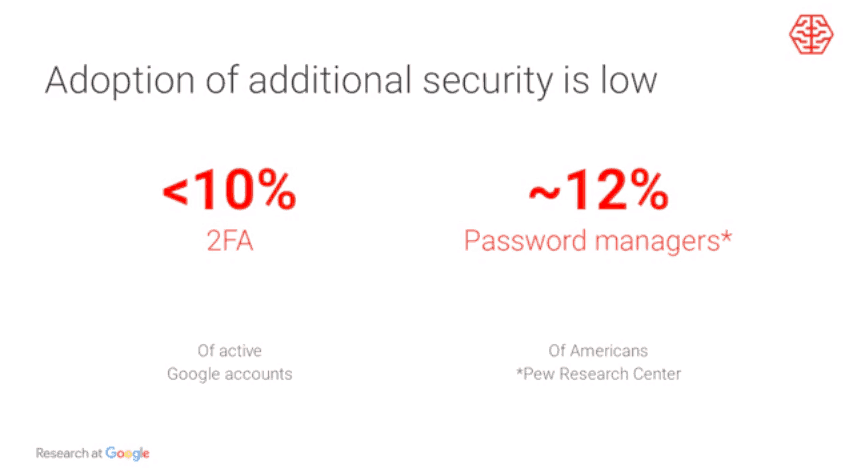
According to a Google Engineer, Grzegorz Milka, more than 90 percent of Gmail users do not use 2FA in their accounts at all. Understandable because most users see it as an extra huddle to accessing their account.
So they avoid it.
Albeit, users still want security. So they’d rather rely on password managers because they make login automatic and require fewer huddles. While a password manager is good, admins must let users know that the more security layers they use, the less likely they’d be hacked.
The Problem with Implementing 2FA
The problem is that most users are not seeing the risk of leaving their email accounts to one authentication mechanism – passwords or passphrases only. Hackers, on the other hand, are looking for accounts with the least resistance to hacking.

The Solution for Admins and Developers
Your job as a developer or admins is to help your users see the risk and understand its costs. So the question comes to “How do I help them see the risk?”
Let them know that attackers might have hacked their accounts already. So having a 2FA in place is a step to stop further compromise even if these hackers compromised their user passwords.
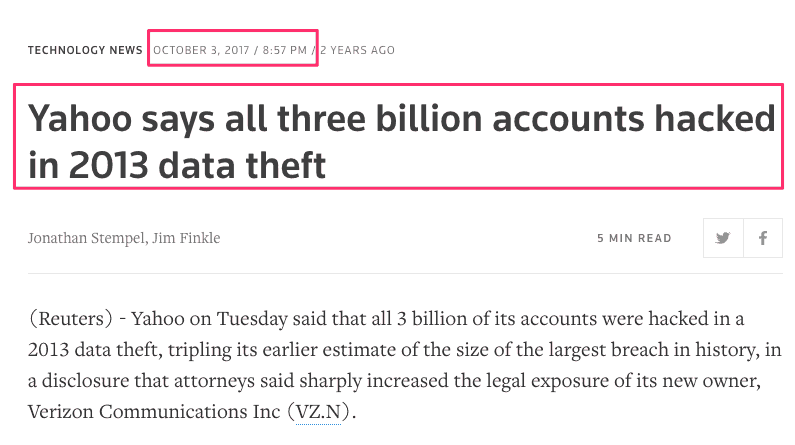
Here’s a case in point. Yahoo had been hacked since 2013 or earlier, but no one noticed until years later in 2017 when the announcement and investigation kicked in. That’s a full four years before people realized they’d been hacked.
Employees need to know that using two-factor authentication puts a demand on the account to notify them, the user, of any unauthorized login attempts.
Secondly, users need to know that they might have been hacked already and may not know it now until later in the future. So setting up a second-factor authentication can help them save their accounts. Security experts say that hackers stole anywhere from 7.5 to 8.5 billion records in 2019 alone.
3. Preventing SMS Spoofing

Hackers understand the power of 2FA, and they’re trying hard to phish their way through that second layer of security. In a study published by Thycotic, 68 percent of black hat hackers said their biggest challenge is multifactor authentication.
Consequently, admins and developers are saddled with the responsibility of helping their users understand and prevent SMS spoofing.
In case SMS spoofing sounds new to you. It’s a phishing technique that hackers use to gain control of their target’s information or devices.
So these hackers would send an SMS message to their targets and making it appear as if the message is coming from a target’s trusted source. A trusted source could be their employer, senior executive, or finance department staff.

For example, a hacker could send SMS messages to your employees that appear to come from you, the admin, asking them to click a link to give some sensitive information. Your employees would click the link, believing the message came from you, and then unknowingly compromise their device, share some sensitive data, or both.
Hackers can use SMS spoofing the same way they use email spoofing,
- Collect sensitive information to aid their hacking activities or sell on the dark web
- Take control of your device and use that access to perpetuate other hacking or identity theft attacks.
So you want to sensitize your users on how to spot and stop a phishing attempt.
The Problem with Preventing SMS Spoofing
The biggest problem with preventing SMS spoofing is ignorance on the part of system users. Additionally, admins are not investing enough resources in educating their users on how to spot and block these spoofing attempts.
Admin and developers might be underestimating the impact of an attack too, and that’s why they are not investing enough in educating their users about SMS phishing.
The Solution for Admins and Developers
Due to the high-level security that 2FA bestows on users, spoofers are desperate to break that line of defense. As an admin or developer, here are your options for preventing an SMS spoof attack.
Invest in Employee or System User Education
Educate your employees and users to not click on SMS links from unknown sources or that they haven’t verified. Let them take this phishing test.
That spoofing test focuses on email spoofing. But it sensitizes users to pay more attention to the messages they receive. Ultimately, attackers want to deceive you into taking an action that grants them access to your sensitive data or device. Hence you want to train your users on how to spot these deceptions.
Use a Signature Message

Set up a signature that goes with every SMS you send to devalue any phishing attempt immediately. For example, “Prevent SMS spoofing: call the number that sent this SMS.”
This prevention technique works because people who spoof phone numbers don’t own them. Tell your users to hang up and call the number back. When they call, they’ll reach the real holder, not the spoofer.
4. The Social Sign-in Puzzle
In the bid to improve authentication, developers introduced social media sign-in. The idea is that users would sign in to third-party websites and apps using their social media accounts, like LinkedIn, Facebook, Twitter, and Gmail.
This arrangement is pretty secure. So the problem here isn’t with the security of the process. But the convenience of the user.
The Problem with Social Sign-In
Social sign-in saves users the hassle of creating new passwords. But these users must remember how they signed up for the service. Hence, this authentication often creates issues for users.

Customer Churn Because of Forgotten Authentication Channel
Your users may signup for your service, but since they don’t use it often, they’d forget how they accessed the site. If they have very little to lose, they’d churn and never return to the service.
Loss of Access to User Account After Loss of Social Account
A user may lose access to the social media account they used to sign up. If that happens, they may churn and stop using the service. Even if they don’t churn, users may define this event as a poor customer experience.
Security Concerns
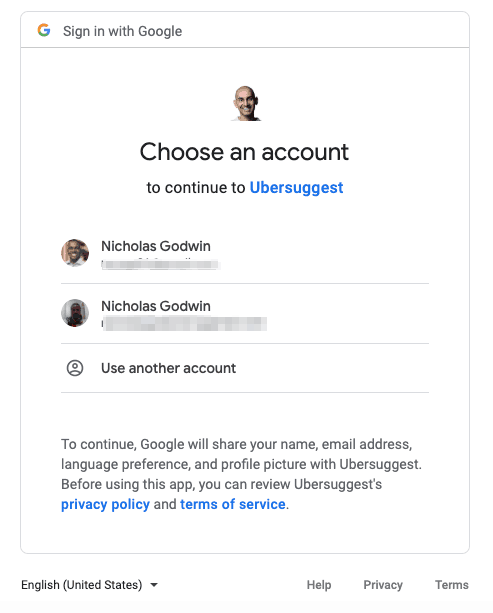
Users may feel unsafe granting third-party apps permissions to their social accounts. This concern may intensify if the app requests access to “control,” “send emails,” or “make posts” on their behalf.
The solution for Admins and Developers

You want to treat the use of social sign-in as an experiment to know how your users find the experience before you discard or adopt it fully. Secondly, admins should provide backup sign-in methods for users in case they lose access to their social accounts.
Developers and admins must provide brief explanations for what they mean when they ask for permission that might deter users from adopting their social sign-in option.
End the Authentication Struggle
Most admins and developers struggle with user authentication because they don’t invest in user security awareness. Users will take more responsibility, the more they understand the risk that comes with being lax with their account security.
In summary, let your users know that
- Clicking unfamiliar links or downloading unexpected attachments could expose them to security risks
- They shouldn’t take phone calls without confirming the identity of the caller or never give sensitive information over a phone call
- If they think their system might be infected or compromised, they should contact an admin
The cost of falling victim to a security exposure outways the cost of preventing it. Hence, you want to invest in prevention, and that includes enforcing 2FA. You also want to test user authentication channels that might improve your security and user authentication experience.

